database for rfid chip ApertureData recently closed its oversubscribed seed round at $8.25 million for a purpose-built database for multimodal AI. The funding round was led by TQ Ventures with . For Gen1a and Gen1b UID Re-Writable cards, Yet Another Mifare Tool (YAMT) uses backdoor commands to write the exact data from the dump onto the card.. You can use those cards for .
0 · where are rfid chips used
1 · types of rfid chips
2 · rfid chips in humans
3 · rfid chips for sale
4 · rfid chip pros and cons
5 · rfid chip meaning
6 · rfid chip manufacturing
7 · pros and cons of rfid
The SE is the only component of an NFC solution that will undergo any evaluation against security requirements and accreditation. The card number (PAN), card holder name, expiry, card .Tapping to pay with your Visa contactless card or payment-enabled mobile/wearable device is a secure way to pay because each transaction generates a transaction-specific, one-time code, .
What data should be stored directly on the RFID transponders and what data should be stored in databases in the backend of a system? The design decision influences many characteristics of . ApertureData recently closed its oversubscribed seed round at .25 million for a purpose-built database for multimodal AI. The funding round was led by TQ Ventures with .
rfid system nz
What data should be stored directly on the RFID transponders and what data should be stored in databases in the backend of a system? The design decision influences many characteristics of the overall RFID system. Thus, data storage considerations are an important part in planning the architecture of such a system. ApertureData recently closed its oversubscribed seed round at .25 million for a purpose-built database for multimodal AI. The funding round was led by TQ Ventures with participation from Westwave Capital, Interwoven Ventures, and a group of high-caliber angel investors. Existing investors also reaffirmed their commitment to ApertureData’s . RFID tags employ a chip and an antenna to broadcast information or respond when prompted to do so by an RFID reader. The chip stores the information, while the antenna responds to requests or repeatedly sends out the tag’s information for any reader within its .
The process of identifying an asset using RFID involves three main components – the tag itself, a reader or scanner device, and a database or software system for storing and managing data. The first step is encoding information on to each unique tag before attaching it to an asset.
salto systems rfid
The Engineering360 SpecSearch database categorizes RFID chips according to the type of device (passive, active, or semi-passive) in which the chips are used. Passive devices are RFID tags without batteries. RFID tags employ a chip and antenna to broadcast information or respond when prompted to do so by an RFID reader. The chip stores the information, while the antenna responds to requests or repeatedly sends out the tag’s information for any reader within its .Radio Frequency Identification (RFID) allows devices to share information without physical contact. This technology has many uses - let's jump in and learn what it is, how it works and how you can use it. In this tutorial, we will learn how to Connect RFID to PHP & MySQL Database with NodeMcu ESP8266. Here I have interfaced RFID-RC522 Module with NodeMcu ESP8266 and then I’m sending data of RFID to MySQL Database. Actually, we are just reading the serial data coming from NodeMcu ESP8266 and then publishing that to MySQL Database through python .
rfid security system project report
Unlock enhanced tracking and security with RFID chips. Explore frequencies, features, and architecture in integrated circuits for seamless solutions.
Radio-frequency identification (RFID) technology is a way for retailers to identify items using radio waves. It transmits data from a RFID tag to a reader, giving you accurate, real-time tracking data of your inventory.What data should be stored directly on the RFID transponders and what data should be stored in databases in the backend of a system? The design decision influences many characteristics of the overall RFID system. Thus, data storage considerations are an important part in planning the architecture of such a system. ApertureData recently closed its oversubscribed seed round at .25 million for a purpose-built database for multimodal AI. The funding round was led by TQ Ventures with participation from Westwave Capital, Interwoven Ventures, and a group of high-caliber angel investors. Existing investors also reaffirmed their commitment to ApertureData’s . RFID tags employ a chip and an antenna to broadcast information or respond when prompted to do so by an RFID reader. The chip stores the information, while the antenna responds to requests or repeatedly sends out the tag’s information for any reader within its .
The process of identifying an asset using RFID involves three main components – the tag itself, a reader or scanner device, and a database or software system for storing and managing data. The first step is encoding information on to each unique tag before attaching it to an asset.
The Engineering360 SpecSearch database categorizes RFID chips according to the type of device (passive, active, or semi-passive) in which the chips are used. Passive devices are RFID tags without batteries.

RFID tags employ a chip and antenna to broadcast information or respond when prompted to do so by an RFID reader. The chip stores the information, while the antenna responds to requests or repeatedly sends out the tag’s information for any reader within its .Radio Frequency Identification (RFID) allows devices to share information without physical contact. This technology has many uses - let's jump in and learn what it is, how it works and how you can use it.
where are rfid chips used
types of rfid chips
In this tutorial, we will learn how to Connect RFID to PHP & MySQL Database with NodeMcu ESP8266. Here I have interfaced RFID-RC522 Module with NodeMcu ESP8266 and then I’m sending data of RFID to MySQL Database. Actually, we are just reading the serial data coming from NodeMcu ESP8266 and then publishing that to MySQL Database through python . Unlock enhanced tracking and security with RFID chips. Explore frequencies, features, and architecture in integrated circuits for seamless solutions.
rfid chips in humans
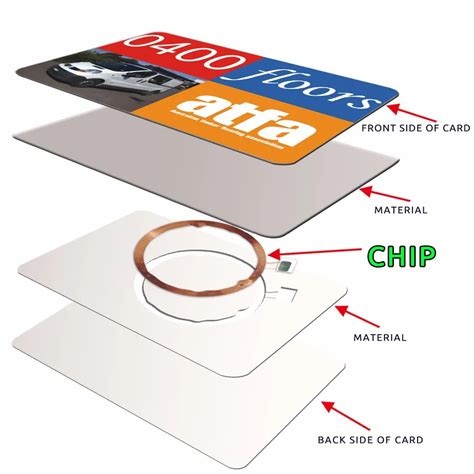
rfid system and device marking
rfid system integration
Although the range of NFC is limited to a few centimeters, standard plain NFC is not protected against eavesdropping and can be vulnerable to data modifications. Applications may use higher-layer cryptographic protocols to establish a secure channel. See more
database for rfid chip|pros and cons of rfid