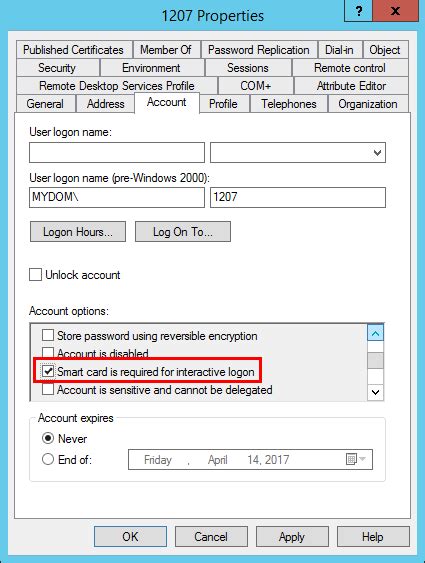
users of smart cards are required to enter a You can set the policy option on a single user by checking the Smart Card is required for interactive logon check box in the user account properties. You can also apply this setting using group policy objects. Over time, NFC tags may accumulate dirt, dust, or debris, which can hinder their functionality and impede successful communication with devices. If you encounter the .
0 · Users of smart cards are required to enter a
1 · Users of Smart Cards Are Required to Enter a
2 · Understanding and Evaluating Virtual S
3 · Smart Card Group Policy and Registry Settings
4 · Smart Card Authentication: A Comprehensive Guide
5 · Smart Card Authentication: A Comprehe
6 · Smart Card Architecture
7 · Setting up Windows laptops to require a smartcard for unlocking
8 · Requiring Smart Cards for Interactive Logons
9 · Multi
10 · How Smart Card Sign
11 · Configure Smart Card Logon on Windows Domains
NFC Tools - KeyBoard Controller is a simple tool that allows you to control your keyboard with an NFC chip. Select your language. Search. Search. menu. Home; News; Company . Tested NFC Readers : ACR122U, ACR122T, ACR1255, .
Users of smart cards are required to enter a ________ to be authenticated. 1.Personal identification number, 2.Trojan horses, 3.Data (base) administration, 4.Provide physical security. This security policy setting requires users to sign in to a computer by using a smart card. Enabled Users can sign in to the computer only by using a smart card. Disabled Users .You can set the policy option on a single user by checking the Smart Card is required for interactive logon check box in the user account properties. You can also apply this setting using group policy objects.Typically, a user who signs in to a computer by using a local account or a domain account must enter a user name and password. These credentials are used to verify the user's identity. For smart card sign-in, a user's credentials are .
Users of smart cards are required to enter a
Users of Smart Cards Are Required to Enter a
Users of smart cards are required to enter a _____ to be authenticated. A) Social Security number B) public key C) personal identification number D) private key A: When you select the Smart Card is required for interactive logon check box in the Active Directory (AD) user account properties, Windows automatically resets the user password to a random complex password.a PKI solution to initialize and manage smart cards; each smart card will contain a private key and the associated certificate; to enable smart card logon so that users open a session on the .
For example, MFA could require users to insert a smart card or a bank card into a card reader (first factor) and then enter a password or a PIN (second factor). An unauthorized user in .
The process: The user puts the smart card into a card reader hooked up to the device or system they want to use. The card reader talks to the smart card, asking the user to enter a password or give fingerprints to prove .Certificate Requirements and Enumeration: Learn about requirements for smart card certificates based on the operating system, and about the operations that are performed by the operating system when a smart card is inserted into the computer.Users of smart cards are required to enter a ________ to be authenticated. 1.Personal identification number, 2.Trojan horses, 3.Data (base) administration, 4.Provide physical security.
dell kb813 smart card keyboard drivers
Understanding and Evaluating Virtual S
dell latitude e6420 smart card driver
This security policy setting requires users to sign in to a computer by using a smart card. Enabled Users can sign in to the computer only by using a smart card. Disabled Users can sign in to the computer by using any method. NOTE: the Windows LAPS-managed local account is exempted from this policy when Enabled.You can set the policy option on a single user by checking the Smart Card is required for interactive logon check box in the user account properties. You can also apply this setting using group policy objects.Typically, a user who signs in to a computer by using a local account or a domain account must enter a user name and password. These credentials are used to verify the user's identity. For smart card sign-in, a user's credentials are contained on the smart card's security chip.Users of smart cards are required to enter a _____ to be authenticated. A) Social Security number B) public key C) personal identification number D) private key
A: When you select the Smart Card is required for interactive logon check box in the Active Directory (AD) user account properties, Windows automatically resets the user password to a random complex password.
a PKI solution to initialize and manage smart cards; each smart card will contain a private key and the associated certificate; to enable smart card logon so that users open a session on the laptop with the smart card, instead of a password (the smart card itself will require entry of a PIN code);For example, MFA could require users to insert a smart card or a bank card into a card reader (first factor) and then enter a password or a PIN (second factor). An unauthorized user in possession of the card would not be able to log in without also knowing the password; likewise, the password is useless without physical access to the card. The process: The user puts the smart card into a card reader hooked up to the device or system they want to use. The card reader talks to the smart card, asking the user to enter a password or give fingerprints to prove who they are.
Certificate Requirements and Enumeration: Learn about requirements for smart card certificates based on the operating system, and about the operations that are performed by the operating system when a smart card is inserted into the computer.Users of smart cards are required to enter a ________ to be authenticated. 1.Personal identification number, 2.Trojan horses, 3.Data (base) administration, 4.Provide physical security. This security policy setting requires users to sign in to a computer by using a smart card. Enabled Users can sign in to the computer only by using a smart card. Disabled Users can sign in to the computer by using any method. NOTE: the Windows LAPS-managed local account is exempted from this policy when Enabled.
Smart Card Group Policy and Registry Settings
You can set the policy option on a single user by checking the Smart Card is required for interactive logon check box in the user account properties. You can also apply this setting using group policy objects.
Typically, a user who signs in to a computer by using a local account or a domain account must enter a user name and password. These credentials are used to verify the user's identity. For smart card sign-in, a user's credentials are contained on the smart card's security chip.
Users of smart cards are required to enter a _____ to be authenticated. A) Social Security number B) public key C) personal identification number D) private key
A: When you select the Smart Card is required for interactive logon check box in the Active Directory (AD) user account properties, Windows automatically resets the user password to a random complex password.a PKI solution to initialize and manage smart cards; each smart card will contain a private key and the associated certificate; to enable smart card logon so that users open a session on the laptop with the smart card, instead of a password (the smart card itself will require entry of a PIN code);For example, MFA could require users to insert a smart card or a bank card into a card reader (first factor) and then enter a password or a PIN (second factor). An unauthorized user in possession of the card would not be able to log in without also knowing the password; likewise, the password is useless without physical access to the card.
dell docking statuion that comes with a smart card reader

users of smart cards are required to enter a|Understanding and Evaluating Virtual S