computer smart card authentication If you use a smart card, the operating system uses Kerberos v5 authentication with X.509 v3 certificates. Virtual smart cards were introduced to alleviate the need for a physical . ALL the Alabama Radio Network Stations, both streaming on the radio dial. Listen to all the Alabama Football the Radio | WhatRadioStation . Opelika / Auburn. WZMG-AM. 96.7. Opp. WAMI-FM. 102.3. Panama City Beach, Fla. WBPC .
0 · smart card multi factor authentication
1 · smart card identity
2 · smart card based identification system
3 · smart card authentication step by
4 · smart card authentication protocol
5 · enable smart card log on
6 · enable smart card authentication
7 · authenticate using your smart card
Radio Shack at 552 GRASS VALLEY HWY, Auburn, CA 95603: store location, business hours, .
If you use a smart card, the operating system uses Kerberos v5 authentication with X.509 v3 certificates. Virtual smart cards were introduced to alleviate the need for a physical .How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.
If you use a smart card, the operating system uses Kerberos v5 authentication with X.509 v3 certificates. Virtual smart cards were introduced to alleviate the need for a physical smart card, the smart card reader, and the associated administration of that hardware. This certificate is needed to authenticate your smart card during logon. Once you’ve completed these steps, you’ll be able to log in to your Windows 10 computer using your smart card. This method is not just more secure, but also convenient. Tips for Enabling Smart Card Logon – Windows 10.
Remote Desktop Services enables users to sign in with a smart card by entering a PIN on the RDC client computer and sending it to the RD Session Host server in a manner similar to authentication that is based on user name and password. Table of Content. Understanding Smart Card Authentication: How Does Smart Card Authentication Work? The process: Implementing Smart Card Authentication: Testing and using the system: Best Practices for Smart Card Authentication: Conclusion: Nowadays, cybersecurity is .Smart Card Authentication is a means of verifying users into enterprise resources using a physical card in tandem with a smart card reader and software.Certificate-based authentication is an encrypted method that enables devices and people to identify themselves to other devices and systems. Two common examples are a smart card or when an employee’s device sends a digital certificate to a network or server.
This Personal Identity Verification (PIV) 101 is intended to help you understand the purpose and uses of a PIV credential at your organization. This PIV 101 focuses on using PIV credentials for logical access such as authenticating to networks or .
to enable smart card logon so that users open a session on the laptop with the smart card, instead of a password (the smart card itself will require entry of a PIN code); to set a local policy which locks the laptop when the card is removed (that one is easy);
Windows normally supports smart cards only for domain accounts. However, there is a third-party library, EIDAuthenticate, which lets you use smart cards with local identities.How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system. If you use a smart card, the operating system uses Kerberos v5 authentication with X.509 v3 certificates. Virtual smart cards were introduced to alleviate the need for a physical smart card, the smart card reader, and the associated administration of that hardware. This certificate is needed to authenticate your smart card during logon. Once you’ve completed these steps, you’ll be able to log in to your Windows 10 computer using your smart card. This method is not just more secure, but also convenient. Tips for Enabling Smart Card Logon – Windows 10.
Remote Desktop Services enables users to sign in with a smart card by entering a PIN on the RDC client computer and sending it to the RD Session Host server in a manner similar to authentication that is based on user name and password. Table of Content. Understanding Smart Card Authentication: How Does Smart Card Authentication Work? The process: Implementing Smart Card Authentication: Testing and using the system: Best Practices for Smart Card Authentication: Conclusion: Nowadays, cybersecurity is .Smart Card Authentication is a means of verifying users into enterprise resources using a physical card in tandem with a smart card reader and software.Certificate-based authentication is an encrypted method that enables devices and people to identify themselves to other devices and systems. Two common examples are a smart card or when an employee’s device sends a digital certificate to a network or server.
This Personal Identity Verification (PIV) 101 is intended to help you understand the purpose and uses of a PIV credential at your organization. This PIV 101 focuses on using PIV credentials for logical access such as authenticating to networks or .to enable smart card logon so that users open a session on the laptop with the smart card, instead of a password (the smart card itself will require entry of a PIN code); to set a local policy which locks the laptop when the card is removed (that one is easy);
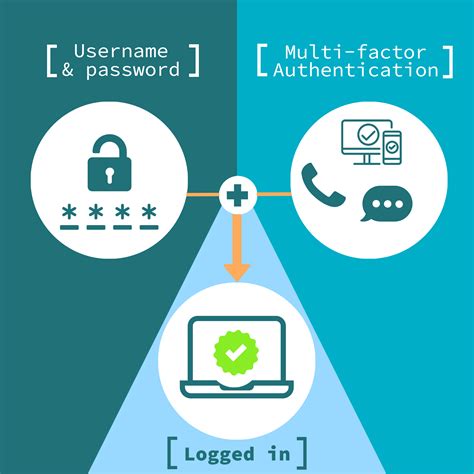
smart card multi factor authentication
smart card identity

smart card based identification system
smart card authentication step by
smart card authentication protocol

The lead shifted to Alabama, and another wild chapter in Iron Bowl history was written. The radio call from Eli Gold will be on repeat in Tuscaloosa for the next year. As called .
computer smart card authentication|enable smart card authentication