security system using rfid ppt The system uses an RFID reader and tags to identify authorized users and grant access by controlling a relay if their RFID code matches stored codes. An LCD displays status messages. The system provides security for organizations by only allowing access to people with valid RFID tags.
Here is everything you need to know in order to listen to Auburn football games on the radio this season. Auburn football radio station 2024 Radio station: WGZZ 94.3 FM, SiriusXM
0 · rfid technology ppt presentation
1 · rfid technology ppt
2 · rfid tags for library books
3 · rfid system in library
4 · rfid ppt download
5 · rfid in library management system
6 · radio frequency identification ppt
7 · library automation using rfid
The Honeywell C30 XP handheld computer is a durable, all-purpose business tool .
The project aims to automate access control for security purposes and unauthorized access prevention through contactless identification of users. The document discusses RFID technology, including how it works, its benefits . The system uses an RFID reader and tags to identify authorized users and grant access by controlling a relay if their RFID code matches stored codes. An LCD displays status messages. The system provides security for .
The document outlines security risks like spoofing, replay attacks, and unauthorized tracking. It emphasizes the need for lightweight cryptography and random number generation on tags to address security challenges in . Enhanced Security: Integrating RFID and NFC with existing security systems . The project aims to automate access control for security purposes and unauthorized access prevention through contactless identification of users. The document discusses RFID technology, including how it works, its . The system uses an RFID reader and tags to identify authorized users and grant access by controlling a relay if their RFID code matches stored codes. An LCD displays status messages. The system provides security for organizations by only allowing access to people with valid RFID tags.
The document outlines security risks like spoofing, replay attacks, and unauthorized tracking. It emphasizes the need for lightweight cryptography and random number generation on tags to address security challenges in RFID systems. Read more. Enhanced Security: Integrating RFID and NFC with existing security systems strengthens overall security. RFID tags and NFC-enabled devices can be programmed with unique identifiers, reducing the risk of unauthorized access.From Smart Homes to Smart Cities: Integrating RFID for Enhanced Security - Let's look at how RFID is helping to improve security everywhere from our homes to the bustling streets of smart cities. | PowerPoint PPT presentation | free to view
Project overview • The main objective of this project is to provide security in an organization by allowing authorized personnel to enter or to access the door to enter into the organization. • For this purpose the authorized personnel are provided with an RFID card.This document describes an RFID-based door security system using an 8051 microcontroller and EM-18 RFID module. The system provides security to organizations by only allowing authorized personnel with valid RFID tags.The document proceeds to discuss security requirements for RFID systems and provides an overview of common privacy and security threats, such as eavesdropping, spoofing, relay attacks, and cloning. It also describes countermeasures to mitigate these threats. Our Solution • “Smart Door” RFID Door Lock • Uses Radio Frequency technology: • RFID provides encrypted, wireless connection • The lock: • Unlocks the door when user approaches • Locks the door when user is away • Key benefit: • Hands free functionality.
1. The document presents details from a student project on an RFID-based security system using Arduino. It lists 5 students and their project topics, all related to using RFID and Arduino for security applications. 2. The system uses RFID tags and sensors along with an Arduino board to control door locks. The project aims to automate access control for security purposes and unauthorized access prevention through contactless identification of users. The document discusses RFID technology, including how it works, its .
The system uses an RFID reader and tags to identify authorized users and grant access by controlling a relay if their RFID code matches stored codes. An LCD displays status messages. The system provides security for organizations by only allowing access to people with valid RFID tags. The document outlines security risks like spoofing, replay attacks, and unauthorized tracking. It emphasizes the need for lightweight cryptography and random number generation on tags to address security challenges in RFID systems. Read more. Enhanced Security: Integrating RFID and NFC with existing security systems strengthens overall security. RFID tags and NFC-enabled devices can be programmed with unique identifiers, reducing the risk of unauthorized access.From Smart Homes to Smart Cities: Integrating RFID for Enhanced Security - Let's look at how RFID is helping to improve security everywhere from our homes to the bustling streets of smart cities. | PowerPoint PPT presentation | free to view
Project overview • The main objective of this project is to provide security in an organization by allowing authorized personnel to enter or to access the door to enter into the organization. • For this purpose the authorized personnel are provided with an RFID card.This document describes an RFID-based door security system using an 8051 microcontroller and EM-18 RFID module. The system provides security to organizations by only allowing authorized personnel with valid RFID tags.The document proceeds to discuss security requirements for RFID systems and provides an overview of common privacy and security threats, such as eavesdropping, spoofing, relay attacks, and cloning. It also describes countermeasures to mitigate these threats.
nfc card hacker
Our Solution • “Smart Door” RFID Door Lock • Uses Radio Frequency technology: • RFID provides encrypted, wireless connection • The lock: • Unlocks the door when user approaches • Locks the door when user is away • Key benefit: • Hands free functionality.
rfid technology ppt presentation
mini nfc amiibo cards
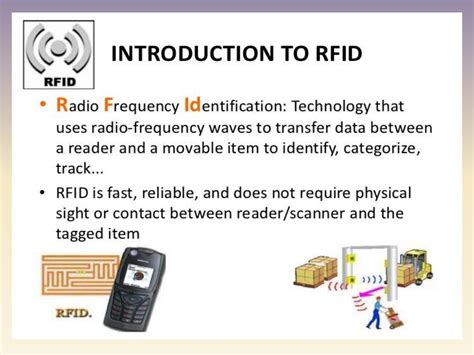
rfid technology ppt
Using NFC on Your IPhone. Hold the NFC tag near your iPhone to read it automatically. If you have an older iPhone, open the Control Center and tap the NFC icon. Move the tag over your phone to activate it. The NFC can .
security system using rfid ppt|rfid technology ppt presentation