smart card ssh config Gnome in RHEL7 was relying on pam_pkcs11 to provide access to Smart Cards through NSS. In RHEL8+, the desktop login is managed by System Security Services Daemon (SSSD). How to . A list of AM and FM radio stations near the city of Auburn, Alabama. Callsign: Zip .
0 · Smart card authentication with SSH
1 · Smart card authentication
2 · Smart Card Logon for SSH
3 · Smart
4 · Securing SSH service with smart cards
5 · Red Hat Enterprise Linux 9
6 · Chapter 6. Configuring smart card authentication with local
7 · About SSH and Smart Card support (RHEL 7)
$24.90
Smart Card Logon for SSH For network engineers, this guide will help you authenticate with your PIV/CAC credential and use SSH to access a remote Linux server from a Windows or macOS computer. For server administrators, this guide will help you configure a Linux server for . The SSH server and client must be configured to permit smart card authentication. Configure the SSH server ¶ The SSH server needs to allow public key authentication set in its .
To configure smart card authentication with local certificates: The host is not connected to a domain. You want to authenticate with a smart card on this host. You want to configure SSH .Gnome in RHEL7 was relying on pam_pkcs11 to provide access to Smart Cards through NSS. In RHEL8+, the desktop login is managed by System Security Services Daemon (SSSD). How to .Administrators can configure mapping rules to reduce the administrative overhead. Table of Contents. PROVIDING FEEDBACK ON RED HAT DOCUMENTATION . . . . . . . . . . . . . . . . . . .
Server configuration. The SSH server and client must be configured to permit smart card authentication. Configure the SSH server. The SSH server needs to allow public key . As smart cards also leverage symmetric key cryptography, they can integrate relatively seamlessly into a secure, convenient SSH configuration. A visual representation of .The following packages must be installed to obtain a smart card configuration on Ubuntu: pcscd: contains the drivers needed to communicate with the CCID smart card readers. opensc .
Smart Card Logon for SSH For network engineers, this guide will help you authenticate with your PIV/CAC credential and use SSH to access a remote Linux server from a Windows or macOS computer. For server administrators, this guide will help you configure a .Server configuration. The SSH server and client must be configured to permit smart card authentication. Configure the SSH server. The SSH server needs to allow public key authentication set in its configuration file and it needs the user’s public key.How to set up smart cards for authentication in Red Hat Enterprise Linux 6 is described in the article : How to configure smart card authentication with openssh on Red Hat Enterprise Linux . Prerequisites Server side. There is no special requirement for the server side in this setup.
The SSH server and client must be configured to permit smart card authentication. Configure the SSH server ¶ The SSH server needs to allow public key authentication set in its configuration file and it needs the user’s public key.
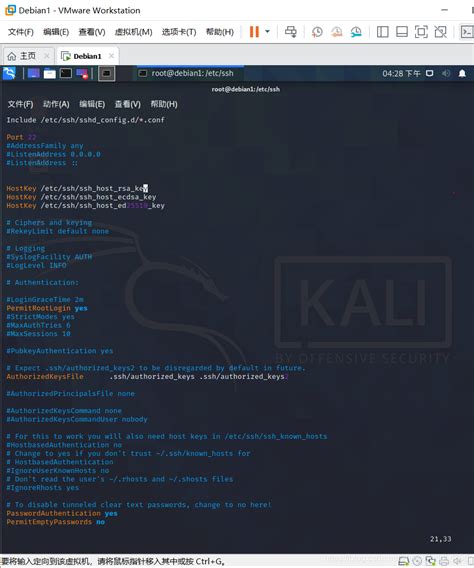
Smart card authentication with SSH
To configure smart card authentication with local certificates: The host is not connected to a domain. You want to authenticate with a smart card on this host. You want to configure SSH access using smart card authentication. You want to configure the smart card with authselect.Gnome in RHEL7 was relying on pam_pkcs11 to provide access to Smart Cards through NSS. In RHEL8+, the desktop login is managed by System Security Services Daemon (SSSD). How to configure system to allow smart cards login of users in IdM is described in RHEL 8 Product documentation, section Configuring Identity Management.Administrators can configure mapping rules to reduce the administrative overhead. Table of Contents. PROVIDING FEEDBACK ON RED HAT DOCUMENTATION . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4 . . . . . . . . . . . . CHAPTER 1. UNDERSTANDING SMART CARD AUTHENTICATION.Server configuration. The SSH server and client must be configured to permit smart card authentication. Configure the SSH server. The SSH server needs to allow public key authentication set in its configuration file and it needs the user’s public key.
As smart cards also leverage symmetric key cryptography, they can integrate relatively seamlessly into a secure, convenient SSH configuration. A visual representation of the public key.The following packages must be installed to obtain a smart card configuration on Ubuntu: pcscd: contains the drivers needed to communicate with the CCID smart card readers. opensc-pkcs11: (optional, depending on your smartcard hardware) contains the smart card drivers, such as Personal Identify Verification (PIV) or Common Access Card (CAC)
Smart Card Logon for SSH For network engineers, this guide will help you authenticate with your PIV/CAC credential and use SSH to access a remote Linux server from a Windows or macOS computer. For server administrators, this guide will help you configure a .
Server configuration. The SSH server and client must be configured to permit smart card authentication. Configure the SSH server. The SSH server needs to allow public key authentication set in its configuration file and it needs the user’s public key.How to set up smart cards for authentication in Red Hat Enterprise Linux 6 is described in the article : How to configure smart card authentication with openssh on Red Hat Enterprise Linux . Prerequisites Server side. There is no special requirement for the server side in this setup. The SSH server and client must be configured to permit smart card authentication. Configure the SSH server ¶ The SSH server needs to allow public key authentication set in its configuration file and it needs the user’s public key.To configure smart card authentication with local certificates: The host is not connected to a domain. You want to authenticate with a smart card on this host. You want to configure SSH access using smart card authentication. You want to configure the smart card with authselect.
Gnome in RHEL7 was relying on pam_pkcs11 to provide access to Smart Cards through NSS. In RHEL8+, the desktop login is managed by System Security Services Daemon (SSSD). How to configure system to allow smart cards login of users in IdM is described in RHEL 8 Product documentation, section Configuring Identity Management.Administrators can configure mapping rules to reduce the administrative overhead. Table of Contents. PROVIDING FEEDBACK ON RED HAT DOCUMENTATION . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4 . . . . . . . . . . . . CHAPTER 1. UNDERSTANDING SMART CARD AUTHENTICATION.Server configuration. The SSH server and client must be configured to permit smart card authentication. Configure the SSH server. The SSH server needs to allow public key authentication set in its configuration file and it needs the user’s public key. As smart cards also leverage symmetric key cryptography, they can integrate relatively seamlessly into a secure, convenient SSH configuration. A visual representation of the public key.

Smart card authentication
1 Timothy 2:1-2. Praise 88.7 - WELL. Welcome to Praise 887.com! Praise 88.7 is excited to bring you the latest contemporary Christian music hits as well as cherished favorites. Listen at 88.7 in East Alabama or online anywhere in the .
smart card ssh config|Chapter 6. Configuring smart card authentication with local