tpm virtual smart cards Virtual smart card technology offers comparable security benefits to physical . Find out which teams are winning the 2024 playoff race. Check out the NFL Playoff Picture for .
0 · virtual tpm windows 10
1 · virtual smart card windows 11
2 · virtual smart card windows 10
3 · tpmvscmgr list virtual smart cards
4 · smart card resource manager download
5 · smart card eim login
6 · smart card authentication step by
7 · install microsoft smart card manager
NFC payments, which rely on near-field communication technology, are a type of contactless payment method. They use a short-range wireless technology that allows two devices, such as a smartphone and a .
Virtual smart card technology offers comparable security benefits to physical . Any TPM that adheres to the TPM main specifications for version 1.2 or version . This blog will mostly concern TPM virtual smart cards. For more information, read Understanding and Evaluating Virtual Smart Cards . Trusted Platform Module - (As Christopher Delay explains in his blog ) TPM is a cryptographic device that is attached at the chip level to a PC, Laptop, Tablet, or Mobile Phone. The TPM securely stores . Thus, private keys protected by the TPM are not exportable. Anti-Hammering: When used in conjunction with passwords or PINs a TPM will lock out if a pin or password is entered incorrectly too many times. Key Isolation: Private keys protected by the TPM are never exposed to the operating system or malware. All private key operations are handled .
Endorsement Certificate: (Medium Assurance) Issuance Policy/Certificate Policy OID 1.3.6.1.4.1.311.21.31 – The TPM has a manufacturer supplied certificate embedded. The Enterprise CA validates the EKCert chain. All CA’s in the chain must be trusted. This method also means that ALL TPM’s from the manufacturer’s chain are trusted.
Smart cards provide seamless and secure authentication to apps, websites, Wi-Fi, and VPN as well as enable the use of S/MIME to sign and encrypt email. With mobile user productivity becoming commonplace in enterprises, many government and high security customers wonder how to embrace mobility while still maintaining a highly secure environment. In the left pane, click Personal , Certificates. c. Select a certificate in the right pane . d. From the Action menu, click All Tasks and then Export . e. Make sure that the private key is exported. Look after the PFX file, because it contains a private key! 3. Finally, importing a key into a smart card is a single command at a command-line.
As I understand, we could build an Azure based virtual environment and purchase PAWs to manage it, while keeping the original root offline (the physical Win10 PC), right? I would like to suggest this cloud based PKI setup to a client that is in the process of expanding their server environment into the cloud, where the case for a on-prem PKI is . Setting up TPM protected certificates using a Microsoft Certificate Authority - Part 2: Virtual Smart Cards NoMoePwds on Jan 24 2020 02:08 PM First published on TECHNET on Jul 15, 2014 Hey Everyone, I am back with part 2 of this 3 part series on TPM protected ce.
virtual tpm windows 10
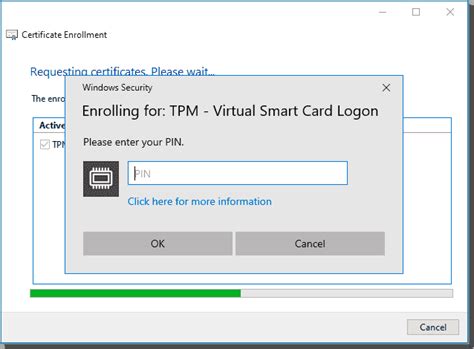
My understanding is that operating system sign-in is relatively straight forward (although there's no option to use username/ password with the VSC, only PIN). Create the certificate template. Create the TPM virtual smart card using tpmvscmgr.exe. Enrol for the certificate on the TPM Virtual Smart Card. Labels: Install the hard drive, install your OS, build your PKI hierarchy, and then remove the hard drive and store it in a safe. The hard drive can be attached to existing hardware when CRLs need to be re-signed. A virtual machine could be used as the Root CA, although you would still want to store it on a separate hard drive that can be stored in a safe. For those of you who use smart cards to help increase the security of your environment, Azure Virtual Desktop now support signing in to Azure AD with smart cards. While this isn't a new feature for Azure AD, configuring Active Directory Federation Services to sign in with smart cards is now supported in Azure Virtual Desktop.
This blog will mostly concern TPM virtual smart cards. For more information, read Understanding and Evaluating Virtual Smart Cards . Trusted Platform Module - (As Christopher Delay explains in his blog ) TPM is a cryptographic device that is attached at the chip level to a PC, Laptop, Tablet, or Mobile Phone. The TPM securely stores .
Thus, private keys protected by the TPM are not exportable. Anti-Hammering: When used in conjunction with passwords or PINs a TPM will lock out if a pin or password is entered incorrectly too many times. Key Isolation: Private keys protected by the TPM are never exposed to the operating system or malware. All private key operations are handled .

Endorsement Certificate: (Medium Assurance) Issuance Policy/Certificate Policy OID 1.3.6.1.4.1.311.21.31 – The TPM has a manufacturer supplied certificate embedded. The Enterprise CA validates the EKCert chain. All CA’s in the chain must be trusted. This method also means that ALL TPM’s from the manufacturer’s chain are trusted. Smart cards provide seamless and secure authentication to apps, websites, Wi-Fi, and VPN as well as enable the use of S/MIME to sign and encrypt email. With mobile user productivity becoming commonplace in enterprises, many government and high security customers wonder how to embrace mobility while still maintaining a highly secure environment. In the left pane, click Personal , Certificates. c. Select a certificate in the right pane . d. From the Action menu, click All Tasks and then Export . e. Make sure that the private key is exported. Look after the PFX file, because it contains a private key! 3. Finally, importing a key into a smart card is a single command at a command-line. As I understand, we could build an Azure based virtual environment and purchase PAWs to manage it, while keeping the original root offline (the physical Win10 PC), right? I would like to suggest this cloud based PKI setup to a client that is in the process of expanding their server environment into the cloud, where the case for a on-prem PKI is .
Setting up TPM protected certificates using a Microsoft Certificate Authority - Part 2: Virtual Smart Cards NoMoePwds on Jan 24 2020 02:08 PM First published on TECHNET on Jul 15, 2014 Hey Everyone, I am back with part 2 of this 3 part series on TPM protected ce. My understanding is that operating system sign-in is relatively straight forward (although there's no option to use username/ password with the VSC, only PIN). Create the certificate template. Create the TPM virtual smart card using tpmvscmgr.exe. Enrol for the certificate on the TPM Virtual Smart Card. Labels: Install the hard drive, install your OS, build your PKI hierarchy, and then remove the hard drive and store it in a safe. The hard drive can be attached to existing hardware when CRLs need to be re-signed. A virtual machine could be used as the Root CA, although you would still want to store it on a separate hard drive that can be stored in a safe.
buy uhf rfid reader
can i swap the rfid chip in key fob
NFC is often used for contactless payments, allowing users to make .
tpm virtual smart cards|virtual tpm windows 10