smart card tectia ssh SSH Tectia Client supports smart cards, USB tokens, and other PKI authentication devices by . Remove ads and more with Turbo. Get the latest version. 5.5.5. Jun 24, 2024. Older versions. Credit Card Reader is an essential tool for accessing public information on EMV banking cards equipped with NFC .
0 · ssh tectia log in
1 · ssh tectia
The ST25R3911B is a highly integrated NFC Initiator / HF reader IC, including the analog front end (AFE) and a highly integrated data framing system for ISO 18092 (NFCIP-1) initiator, ISO 18092 (NFCIP-1) active target, ISO 14443A and B .When selecting a user to charge/credit, the operator may user a username or a Card/ID Number. Using a card reader here allows the operator to identify a user without having to type in the number, e.g. by asking the user to present their card for identification. Any keyboard emulating .
SSH Tectia Client supports smart cards, USB tokens, and other PKI authentication devices by .Using Keys on Smart Cards. To enable public-key authentication using a token, go through the following steps. Note that steps 2 and 4 are not necessary if the user certificate is stored on t.Using Keys on Smart Cards. To enable public-key authentication using a token, go through the .SSH Tectia Client supports smart cards, USB tokens, and other PKI authentication devices by supporting PKCS#11 and MSCAPI for interfacing with authentication keys. Strong, two-factor authentication overcomes the inherent security issues of password authentication.
Using Keys on Smart Cards. To enable public-key authentication using a token, go through the following steps. Note that steps 2 and 4 are not necessary if the user certificate is stored on the token and the Secure Shell server allows certificate .It offers an easy method for utilizing also digital certificates and smart cards. The authentication forwarding functionality allows the forwarding of public-key authentication over several Secure Shell connections. The Connection Broker is started automatically when .Smart Card Logon for SSH For network engineers, this guide will help you authenticate with your PIV/CAC credential and use SSH to access a remote Linux server from a Windows or macOS computer. For server administrators, this guide will help you configure a .Installing SSH Tectia Client >> Getting Started >> Connecting to a Remote Host Defining Quick Connect Options Generating Keys >> Enrolling Certificates >> Uploading Your Public Key >> Using Public-Key Authentication with SSH Accession Lite >> Using Keys on Smart Cards Using SSH2 Software Keys Examples of Use Configuring SSH Tectia Client >>
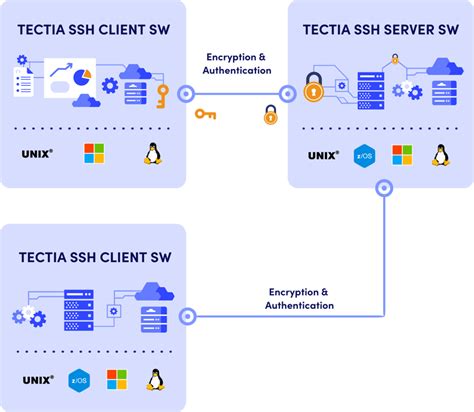
One of the authentication methods supported by the SSH protocol is public key authentication. A public key is copied to the SSH server where it is stored and marked as authorized. The owner of the corresponding private key in the smart card can then SSH login to the server.With Tectia SSH, you can rapidly encrypt and stream high-volume secure file transfers via SSH File Transfer Protocol (SFTP) and Secure copy protocol (SCP) command-line tools. Tectia also comes with a checkpoint/restart mechanism for transferring very .For general information on Tectia Client and its features, refer to Tectia Client/Server Product Description. 1.1 Documentation Conventions The following typographical conventions are used in Tectia documentation:
Tectia Zero Trust Edition allows an efficient role-based access control (RBAC) to bring scalability to managing access to large server estates. By operating without permanent credentials like SSH keys or passwords, Tectia Zero Trust eliminates the costly process of managing or rotating credentials while It is possible to use smartcards to authenticate over ssh, however in order to do it you would need SSH software that supports that functionality. Tectia is one example that supports this configuration.SSH Tectia Client supports smart cards, USB tokens, and other PKI authentication devices by supporting PKCS#11 and MSCAPI for interfacing with authentication keys. Strong, two-factor authentication overcomes the inherent security issues of password authentication.
Using Keys on Smart Cards. To enable public-key authentication using a token, go through the following steps. Note that steps 2 and 4 are not necessary if the user certificate is stored on the token and the Secure Shell server allows certificate .It offers an easy method for utilizing also digital certificates and smart cards. The authentication forwarding functionality allows the forwarding of public-key authentication over several Secure Shell connections. The Connection Broker is started automatically when .Smart Card Logon for SSH For network engineers, this guide will help you authenticate with your PIV/CAC credential and use SSH to access a remote Linux server from a Windows or macOS computer. For server administrators, this guide will help you configure a .Installing SSH Tectia Client >> Getting Started >> Connecting to a Remote Host Defining Quick Connect Options Generating Keys >> Enrolling Certificates >> Uploading Your Public Key >> Using Public-Key Authentication with SSH Accession Lite >> Using Keys on Smart Cards Using SSH2 Software Keys Examples of Use Configuring SSH Tectia Client >>

ssh tectia log in
One of the authentication methods supported by the SSH protocol is public key authentication. A public key is copied to the SSH server where it is stored and marked as authorized. The owner of the corresponding private key in the smart card can then SSH login to the server.With Tectia SSH, you can rapidly encrypt and stream high-volume secure file transfers via SSH File Transfer Protocol (SFTP) and Secure copy protocol (SCP) command-line tools. Tectia also comes with a checkpoint/restart mechanism for transferring very .For general information on Tectia Client and its features, refer to Tectia Client/Server Product Description. 1.1 Documentation Conventions The following typographical conventions are used in Tectia documentation:Tectia Zero Trust Edition allows an efficient role-based access control (RBAC) to bring scalability to managing access to large server estates. By operating without permanent credentials like SSH keys or passwords, Tectia Zero Trust eliminates the costly process of managing or rotating credentials while
auburn kick six radio call youtube
ssh tectia
Of course we love print, but because we also love the web we wanted to bring those two worlds together, making paper more useful than it’s .A customer today in my shop had a NFC Smart bank card that had multiple bank cards on it .
smart card tectia ssh|ssh tectia