implementation of improved des algorithm in securing smart card data Although smart cards have already provided secure portable storage device, security is still a major concern to electronic data systems. There is a need to improve data security against .
A quote from the docs. Android 4.4 and higher provide an additional method of card emulation that doesn't involve a secure element, called host-based card emulation. This allows any .The purpose of NFC technology is all in the name: Near-Field Communication. Basically, it allows two electronic devices to communicate with each other, without needing Wi-Fi or Bluetooth, so long as they are within range of about 4 inches. Since NFC chips are extremely small, they can be embedded into all . See more
0 · Research on Improvement of DES Encryption Algorithm
1 · Implementation of Improved DES Algorithm in Securing Smart
2 · Implementation of Improved DES Algorithm in Securing
3 · Enhanced DES Implementation Secure Against High
4 · CCIS 340
5 · An Improved Data Encryption Standard to Secure Data Using Sm
6 · An Improved Data Encryption Standard to Secure Data Using
7 · An Enhanced Simplified Data Encryption Standard
dot is a seamless way to share contact info A single dot card will last you a lifetime of connections. No subscriptions to share your dot profile. dot profiles hold all your personal info and social media links. No app required to share your .
There is a need to improve data security against accidental or unlawful destruction or alteration during transmission or while in storage. The Odd-Even substitution proved to have provided .
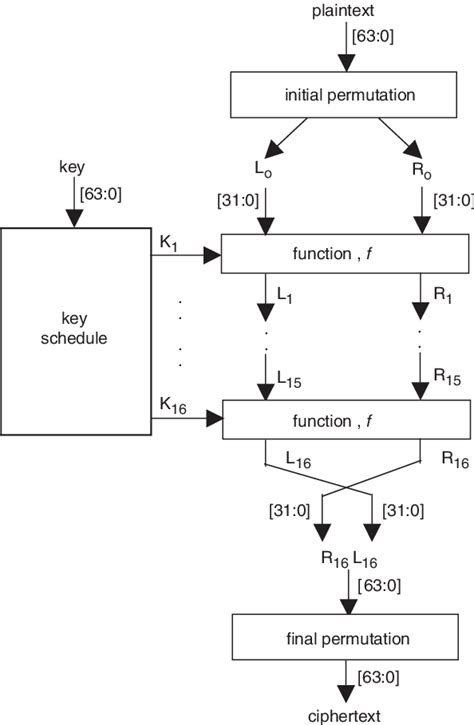
Although smart cards have already provided secure portable storage device, security is still .The software simulation result proved that the inclusion of the Odd-Even substitution to DES has provided additional confusion technique to DES and was essential in providing adequate .
The test results show that the data security technique using dynamic keys ensures that read and write access to the smart card can only be done if the keys match the rules, and this .
In this study, a data security technique using dynamic keys is proposed by changing the key and access conditions on the smart card according to predetermined rules.Although smart cards have already provided secure portable storage device, security is still a major concern to electronic data systems. There is a need to improve data security against .An improved Data Encryption Standard has been developed by incorporating an ODD/EVEN bit conversion to the existing DES algorithm. The proposed algorithm is expected to provide .
In this paper, after showing some attacks on Akkar et al. ’s improved DES implementation from FSE’04, we list and prove some basic requirements for a DES implementation using masking . An improved Data Encryption Standard has been developed by incorporating an ODD/EVEN bit conversion to the existing DES algorithm. The proposed algorithm is expected . This paper proposes An Enhanced Simplified Data Encryption Standard (SDES) algorithm to protect the data in smart cards. It augments complement and shift operations to the existing SDES.
This paper introduces the encryption principle and characteristics of DES encryption algorithm, analyzes the improved DES encryption algorithm proposed by W. Yihan and L. Yongzhen, and .There is a need to improve data security against accidental or unlawful destruction or alteration during transmission or while in storage. The Odd-Even substitution proved to have provided .The software simulation result proved that the inclusion of the Odd-Even substitution to DES has provided additional confusion technique to DES and was essential in providing adequate .The test results show that the data security technique using dynamic keys ensures that read and write access to the smart card can only be done if the keys match the rules, and this .
In this study, a data security technique using dynamic keys is proposed by changing the key and access conditions on the smart card according to predetermined rules.Although smart cards have already provided secure portable storage device, security is still a major concern to electronic data systems. There is a need to improve data security against .
Research on Improvement of DES Encryption Algorithm
An improved Data Encryption Standard has been developed by incorporating an ODD/EVEN bit conversion to the existing DES algorithm. The proposed algorithm is expected to provide .In this paper, after showing some attacks on Akkar et al. ’s improved DES implementation from FSE’04, we list and prove some basic requirements for a DES implementation using masking . An improved Data Encryption Standard has been developed by incorporating an ODD/EVEN bit conversion to the existing DES algorithm. The proposed algorithm is expected . This paper proposes An Enhanced Simplified Data Encryption Standard (SDES) algorithm to protect the data in smart cards. It augments complement and shift operations to .
rilascio smart card
This paper introduces the encryption principle and characteristics of DES encryption algorithm, analyzes the improved DES encryption algorithm proposed by W. Yihan and L. Yongzhen, and .There is a need to improve data security against accidental or unlawful destruction or alteration during transmission or while in storage. The Odd-Even substitution proved to have provided .
The software simulation result proved that the inclusion of the Odd-Even substitution to DES has provided additional confusion technique to DES and was essential in providing adequate .
rsrtc smart card form
Implementation of Improved DES Algorithm in Securing Smart
The test results show that the data security technique using dynamic keys ensures that read and write access to the smart card can only be done if the keys match the rules, and this . In this study, a data security technique using dynamic keys is proposed by changing the key and access conditions on the smart card according to predetermined rules.Although smart cards have already provided secure portable storage device, security is still a major concern to electronic data systems. There is a need to improve data security against .

An improved Data Encryption Standard has been developed by incorporating an ODD/EVEN bit conversion to the existing DES algorithm. The proposed algorithm is expected to provide .
In this paper, after showing some attacks on Akkar et al. ’s improved DES implementation from FSE’04, we list and prove some basic requirements for a DES implementation using masking . An improved Data Encryption Standard has been developed by incorporating an ODD/EVEN bit conversion to the existing DES algorithm. The proposed algorithm is expected . This paper proposes An Enhanced Simplified Data Encryption Standard (SDES) algorithm to protect the data in smart cards. It augments complement and shift operations to .
Implementation of Improved DES Algorithm in Securing

Contactless payments, including Visa contactless cards, Google Pay and Apple Pay, use the same NFC (Near Field Communication) technology. Samsung Pay, however, works with both NFC technology and MST (Magnetic Secure Transition) technology, which can be .
implementation of improved des algorithm in securing smart card data|Implementation of Improved DES Algorithm in Securing Smart