authentication system and method for smart card transactions Authentication system and method for smart card transactions. Abstract. An authentication system includes a portable information device, such as a smart card, that is configured to. NFL Playoff Schedule 2017: Dates, Kickoff Times, TV Listings, Results For Each Game . WILD-CARD ROUND Saturday, Jan. 7 AFC: Houston Texans 27, Oakland Raiders 14 . NFC .
0 · What is Smart card authentication?
1 · Understanding Smart Card Authenticatio
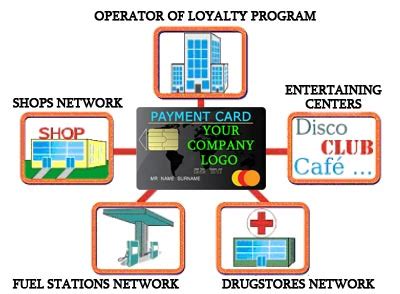
2 · Smart Cards in Payment Systems
3 · How does Smart Card Authentication w
4 · Authentication system and method for smart card transactions
PC-linked contactless smart card and NFC Tags reader/writer, developed on the 13.56 MHz contactless technology. . NFC USB keyboard emulator - UID Reader for Chips ISO 14443 Part 4 Type A and B cards and MIFARE® series. .USB HID card reader (cardIO) for official Konami eAmusement slotted and wavepass readers (ICCA, ICCB, ICCC) See more
Authentication system and method for smart card transactions. Abstract. An authentication system includes a portable information device, such as a smart card, that is configured to.The three-tiered authentication system promotes security in smart card transactions. Inventors: .
Authentication system and method for smart card transactions. Abstract. An authentication system includes a portable information device, such as a smart card, that is configured to.The three-tiered authentication system promotes security in smart card transactions. Inventors: Deo, Vinay (Redmond, WA) Seidensticker, Robert B. (Woodinville, WA) Simon, Daniel R. (Redmond, WA)
Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and industry certifications. Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify.Smart card authentication is an important part of cybersecurity, providing an extra layer of protection in our increasingly digital world. It involves the use of smart cards, which are small, pocket-sized cards with embedded integrated circuits or "chips" that can process data.Smart card authentication is a security process that uses a physical smart card to verify a user's identity before granting access to systems or resources. These cards contain embedded integrated circuits that securely store data, enabling secure access and transaction processing.
Password-based authentication is the most common and simplest method of authentication for securing your network monitoring program. Here, the "password" might be a username-password combination, passcode, or PIN. It's intuitive, as many users are already familiar with such login methods.
The user flow of smart card authentication is as follows. An employee’s identity is tied to company-deployed smart card, which has an embedded chip that is capable of storing and presenting cryptographic keys.
Near Field Communication (NFC), biometrics, and PIN are used in the authentication method for financial transactions. To make a transaction, a smart phone app is used to enter the money, and then the receiver’s information is retrieved using NFC. This chapter provides a first introduction to a wide range of smart cards and tokens, considering the various types, capabilities, popular applications and the practicality of their development and deployment, covered in detail within .Authentication system and method for smart card transactions. Abstract. An authentication system includes a portable information device, such as a smart card, that is configured to.The three-tiered authentication system promotes security in smart card transactions. Inventors: Deo, Vinay (Redmond, WA) Seidensticker, Robert B. (Woodinville, WA) Simon, Daniel R. (Redmond, WA)
Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and industry certifications. Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify.Smart card authentication is an important part of cybersecurity, providing an extra layer of protection in our increasingly digital world. It involves the use of smart cards, which are small, pocket-sized cards with embedded integrated circuits or "chips" that can process data.Smart card authentication is a security process that uses a physical smart card to verify a user's identity before granting access to systems or resources. These cards contain embedded integrated circuits that securely store data, enabling secure access and transaction processing.
Password-based authentication is the most common and simplest method of authentication for securing your network monitoring program. Here, the "password" might be a username-password combination, passcode, or PIN. It's intuitive, as many users are already familiar with such login methods.The user flow of smart card authentication is as follows. An employee’s identity is tied to company-deployed smart card, which has an embedded chip that is capable of storing and presenting cryptographic keys. Near Field Communication (NFC), biometrics, and PIN are used in the authentication method for financial transactions. To make a transaction, a smart phone app is used to enter the money, and then the receiver’s information is retrieved using NFC.

What is Smart card authentication?
Understanding Smart Card Authenticatio

Smart Cards in Payment Systems
How does Smart Card Authentication w
Authentication system and method for smart card transactions
1985 Topps #33 Walter Payton Chicago Bears Football Card NFC All Pro HOF #33 [eBay] $0.99: Report It: 2024-09-02 . Walter Payton [All Pro] #33 (1985 Topps | Football Cards) prices are based on the historic sales. The prices .About Press Copyright Contact us Creators Advertise Developers Terms Privacy Policy & Safety How YouTube works Test new features NFL Sunday Ticket Press Copyright .
authentication system and method for smart card transactions|What is Smart card authentication?